Executive Summary on Cybersecurity for any business - NIST
As a business owner you have concerns about protecting your sensitive and hard-won data. If you are a manufacturer your proprietary data may have cost millions to develop. If you are a doctor with multiple clinics disclosure of your sensitive data can COST you millions in regulatory fines. And you hear from time to time about various cybersecurity tools…antivirus, firewalls, disaster recovery, cloud systems. What does it all mean?
It is crucial to be aware that proper cybersecurity is an approach and a method…it does not occur because of a product or a service.
The Basics
Understanding that proper cybersecurity results from a methodical and consistent approach is key to dispelling dangerous myths and amping down your tension about the security of your information. Here are some important concepts regarding cybersecurity:
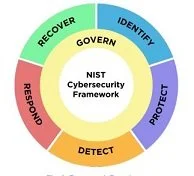
Using the NIST CyberSecurity Framework (CSF) is beneficial for any type of organization due to its applicability to nearly any type of business, and it helps to meet other cyber standards such as CMMC, etc.
There is no “silver bullet” to cybersecurity - no single product will solve the problem
Cybersecurity is a continuous process
Proper cybersecurity is automated to the maximum extent possible
Proper cybersecurity is integrated between products and services to provide information which is actionable
Be aware that your vendors and supply-chain both entail risk
Stay focused on outcomes
Focusing on what is needed at the executive level the basics can be attended to by doing the following:
Governance
As an executive or a business owner, you have the best view of the business objectives of the company as well as the markets you serve. So be aware:
Ensure that your senior IT staff and outside consultants are involved in business planning as cybersecurity must be part of this
Be sure that you are periodically briefed by your senior IT staff or your 3rd-party cybersecurity consultants on current key risks which are being observed, and their recommendations for dealing with them
Ensure that adequate financial resources are brought to bear based upon these recommendations
Cybersecurity is supported via appropriate written policies…this provides for standardization in infrastructure and cyber preparations and acts as a solid guideline
Ensure that any compliance mandates are properly supported
Identify
The NIST function of “Identify” is related to understanding both assets and business risks
Your organization should be using a remote monitoring tool which can identify and report on every item which is attached to your business networks
The remote monitoring should be able to provide reporting and alerting on all key performance metrics for every server, workstation, and related device on your network, even while used off the network (i.e. tablets)…this provides automated asset reporting by make, model, serial number and component down to the hard drives and memory as well as all installed software
Periodic risk assessments are essential and should provide recommendations for improvement which are followed and tracked in writing. These require review with your IT staff for planning and action
Supply chain - your supply chain and your vendors are a source of risk…be conversant with how your written policy documents and procedures address this risk and discuss risk with your vendors
Protect
The “Protect” function deals with much of the “hands-on” cybersecurity systems and tools
Training - One of the most under-emphasized aspects of cyber is user training and awareness. A continuous, well-documented cyber training regimen should be in place, and as an executive you need to be aware of training completion rates with your staff, and emphasize its importance by being first to complete this training. Be the positive example for your organization
Identity management, access control, and credentials - periodic assessments will reflect changes to staffing and access permissions…of course multifactor authentication should be used with every possible system if it deals with sensitive operations or data. Do your users utilize insecure systems to store credentials?
Security platforms - this varies based upon the business, but these systems should be integrated to the maximum extent possible. Your IT staff or 3rd-party cybersecurity consultants should be able to explain your defensive measures and their key successes. They should also explain how they integrate to provide value and superior protection
Technology resilience - traditionally this encompasses business continuity (formerly disaster recovery) for all of your key business systems, whether on-premise or cloud-based. If your data resides in the cloud, then redundant internet or internet failover become essential
Security of your various platforms - both your business systems and their security platforms need to have their security adjusted and tightened on a periodic basis
Detect
Detection and Analysis of threats to the business
As an executive request periodic briefings on developing trends and threats…your staff will appreciate your time and interest…having good communications on a consistent basis pays off in the event of an incident
Using remote monitoring and management is essential…this will detect new (and possibly unexpected) devices on the network
Using a Security Information Event Management (SIEM) system ties together and automatically analyzes audit logs from firewalls, wireless, servers, workstations, antivirus, email systems and other systems which use sensitive data. This system detects unusual access attempts, software, and other threat behavior
A Security Operations Center (SOC) is often used to provide oversight of the SIEM and other cyber systems…this acts as a critical resource in the event problems develop, and acts as a human backstop to escalate specific threats and recommend solutions
Respond
Taking action when a cybersecurity incident is suspected or detected
You are the owner or executive - set the example for your organization in terms of professional demeanor and communications
Assist your IT team by enforcing the use of documented procedures, and encouraging the use of all reasonable resources to resolve the situation
Be aware that threat actors want to encourage panic and poor decision-making...avoid that trap
When an incident is resolved, as an executive it is essential to review the reporting done on the incident, any ramifications, and how to avoid similar incidents in the future by supporting recommended correction measures
Recover
Ensuring that affected systems have been properly recovered
The recovery from an incident entails verifying all affected operations have resumed normal function
As an executive it is critical that you manage communications by keeping staff and executives from micromanaging or hindering recovery efforts
After resolution review any key learning points and recommendations with your IT staff
Be sure to support efforts at training and tools to avoid this issue in the future, and encourage a culture which embraces education and improvement