Tips to "cut the phishing line"
Phishing is becoming a far more serious issue over the past year with attackers having developed sophisticated means to bypass email security systems with emails which are authentic enough to fool casual users. To reduce this risk it is absolutely critical for users to be trained to recognize phishing emails. Some tips from our client training sessions:
Tip 1 - Never Trust the Alias - before assuming an email is authentic, NEVER trust the alias (the senders name)…look at the actual FROM address. Does it have added characters or substituted letters? Is it from an actual domain? Is it from a gmail or other public email address? If the email is supposed to be from Fred Jones whose email address is fred.jones@private.com, mouse over the sender address. If it comes from fxdw@public.com then it is a phishing email.
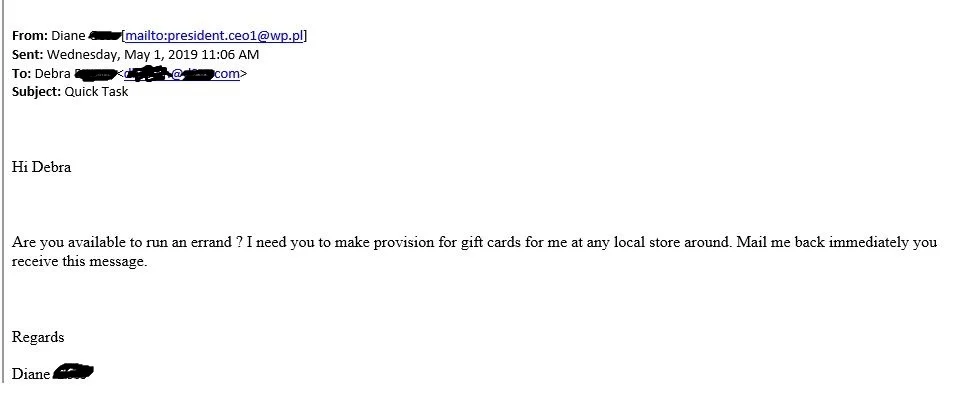
Tip 2 - Is it out of character? Does it appear to be from a trusted executive in your organization who is asking you to purchase gift cards, perform a wire transfer, send a payment of some kind? Any organization should have policies which control payments with a specific approval process. Gift card scams are an easy way to trick users - basically an internal email requests $800 of gift cards be purchased by the company credit card, the scratch-offs removed, and the codes photographed and emailed back to the sender (basically the email goes to fxdw@public.com. Untraceable and easy. Ask the referenced executive before acting.
Tip 3 - Does the email have an attachment which is either locked or encrypted, and the code to open it is in the body of the email? This is akin to locking up your house and taping the key to the front door. This approach works because email security systems cannot evaluate either encrypted email or password-protected emails. Normally security systems allow these to pass, so don’t fall for this trick.
Tip 4 - Is the email asking you to click on a link to confirm credentials? Systems will not normally require this…never trust an email which asks you to complete a form in order to confirm your credentials. This is no different than someone calling you on the phone and asking for them. The objective of the attacker is to acquire these credentials and try them against Paycom, Facebook, your bank, etc. This is an automated process in which the email which reaches you is just one of the last steps. Within 5-10 minutes of entering the credentials, they are used against every account the attacker knows that you use. So if you tend to use identical credentials for all your “stuff” (bad idea), they will quickly have access.
No email security system is perfect, and users are the last line of defense! Stay safe!